[ad_1]
This publish was written in collaboration with Databricks accomplice Immuta. We thank Sam Carroll, Companion Options Architect, Immuta, for his contributions.
Think about you’re a NOC/SOC analyst in a globally distributed group. You simply obtained an alert, however you possibly can’t entry the info due to compliance roadblocks – and in consequence, your response time lags. However, what if there was a option to implement knowledge privateness and catch the baddies?
On this weblog, you’ll find out how Databricks and Immuta remedy the difficult downside of huge scale knowledge evaluation and safety. Databricks supplies a lakehouse platform for large knowledge analytics and synthetic intelligence (AI) workloads on a collaborative cloud-native platform. Immuta ensures that knowledge is accessed by the correct folks, on the proper time, for the correct causes. The Databricks Lakehouse Platform, coupled with Immuta’s person and knowledge entry controls, empowers organizations to seek out insights in essentially the most stringent zero belief and compliance environments.
The rising want for Zero Belief architectures
Fashionable Community Operation Facilities (NOCs) and cybersecurity groups acquire lots of of terabytes of information per day, amounting to petabytes of information retention necessities for regulatory and compliance functions. With ever rising petabytes that comprise troves of delicate knowledge, organizations battle to take care of the usability of that knowledge whereas conserving it safe.
In accordance with Akamai, a Zero Belief safety mannequin is a technique that controls entry to data by making certain a strict id verification course of is adopted. To take care of knowledge safety, Zero Belief structure (ZTA) is rising as a requirement for organizations. The ZTA maturity mannequin is underpinned by visibility and analytics and governance. However this mannequin has operational implications, because it requires organizations to undertake applied sciences that allow massive scale knowledge entry and safety.
We’ll use a consultant instance of community knowledge for example how a community safety staff makes use of Databricks and Immuta to supply a safe and performant huge knowledge analytics platform throughout a number of compliance zones (totally different international locations). If you wish to play alongside and see the info, you possibly can obtain it from the Canadian Institute for Cybersecurity. By the tip of this weblog, you’ll know the right way to:
- Register and classify a delicate knowledge supply with Immuta
- Implement knowledge masking
- Implement least privilege for knowledge entry
- Construct a coverage to stop unintentional knowledge discovery
- Execute a Databricks pocket book in Databricks SQL with least privilege
- Detect a DDoS risk whereas sustaining least privilege
Enabling Zero Belief with Databricks and Immuta
On this situation, there are community analysts in america, Canada, and France. These analysts ought to solely see the alerts for his or her particular area. Nevertheless, when we have to carry out incident evaluation, we’ll must see data on the occasions in different areas. Because of the delicate nature of this knowledge set, we should always have a least privilege entry mannequin utilized in our Databricks setting.
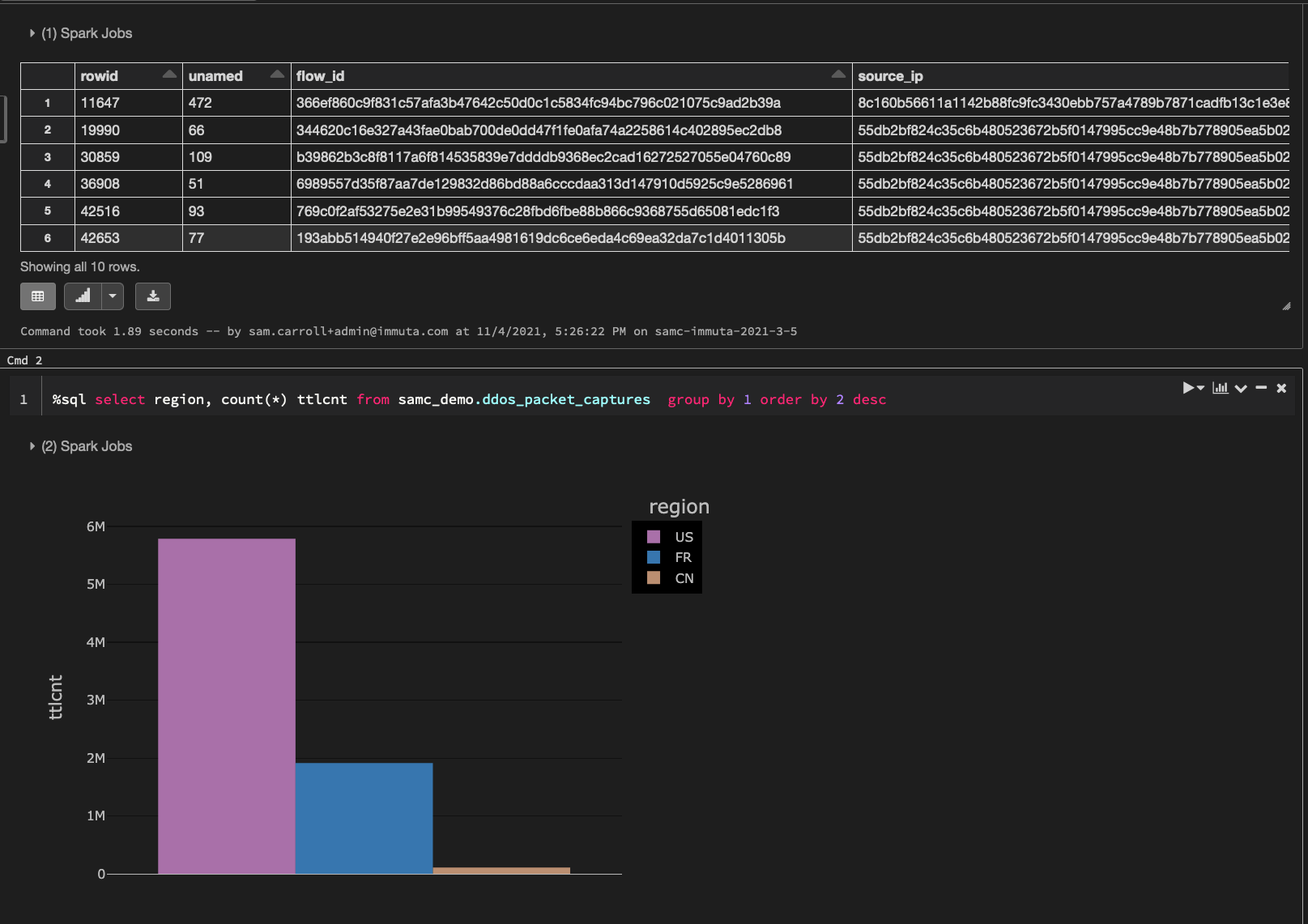
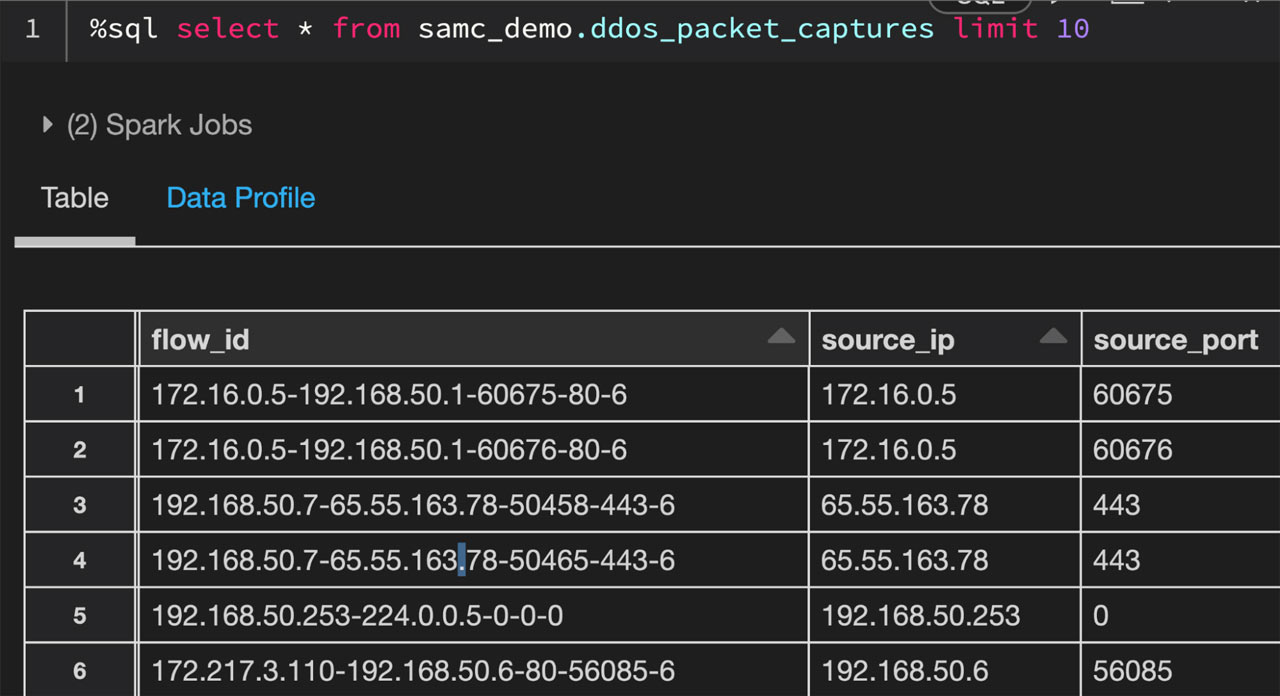
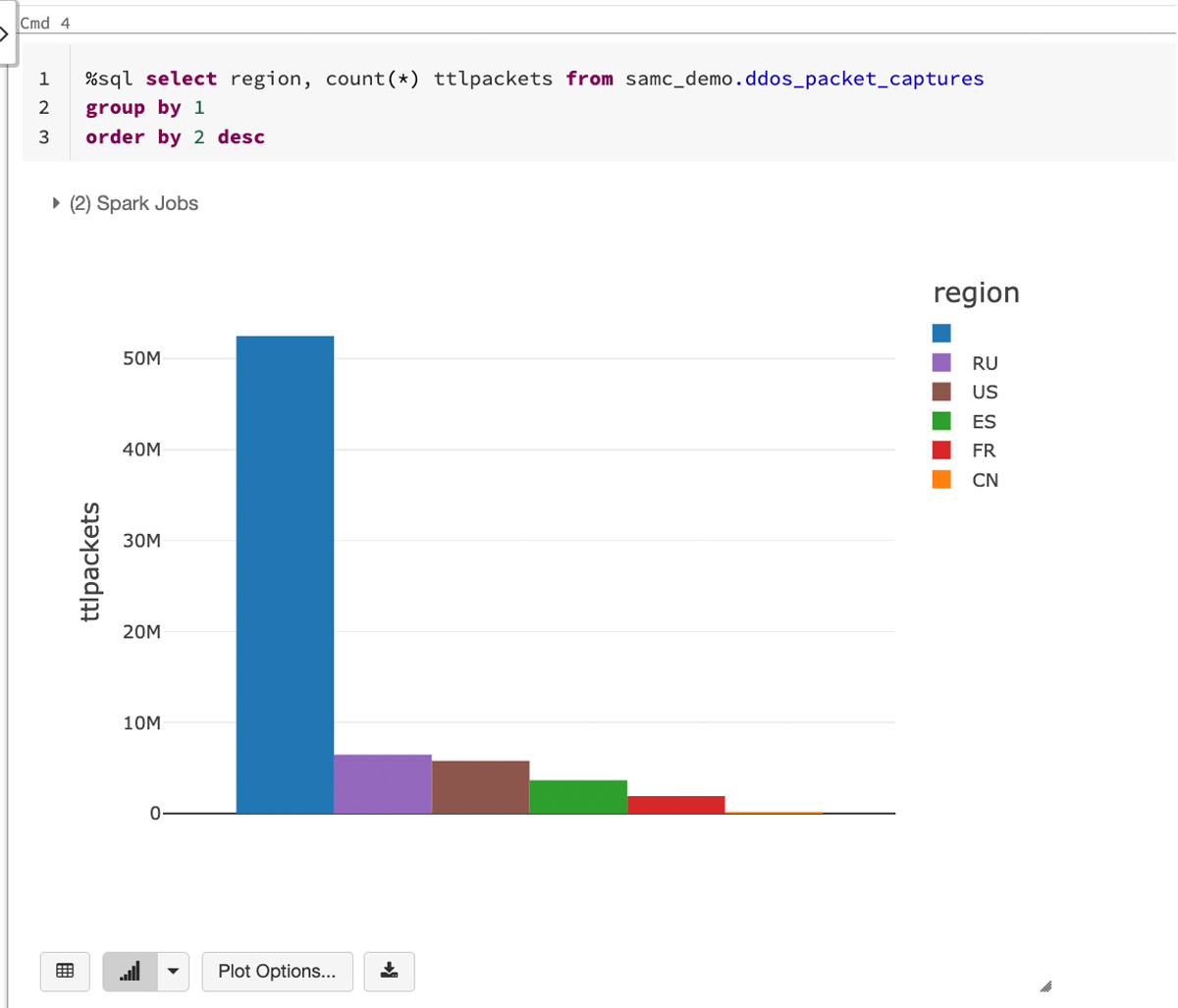
Let’s check out the packet seize knowledge in Databricks that we are going to be utilizing for this weblog:
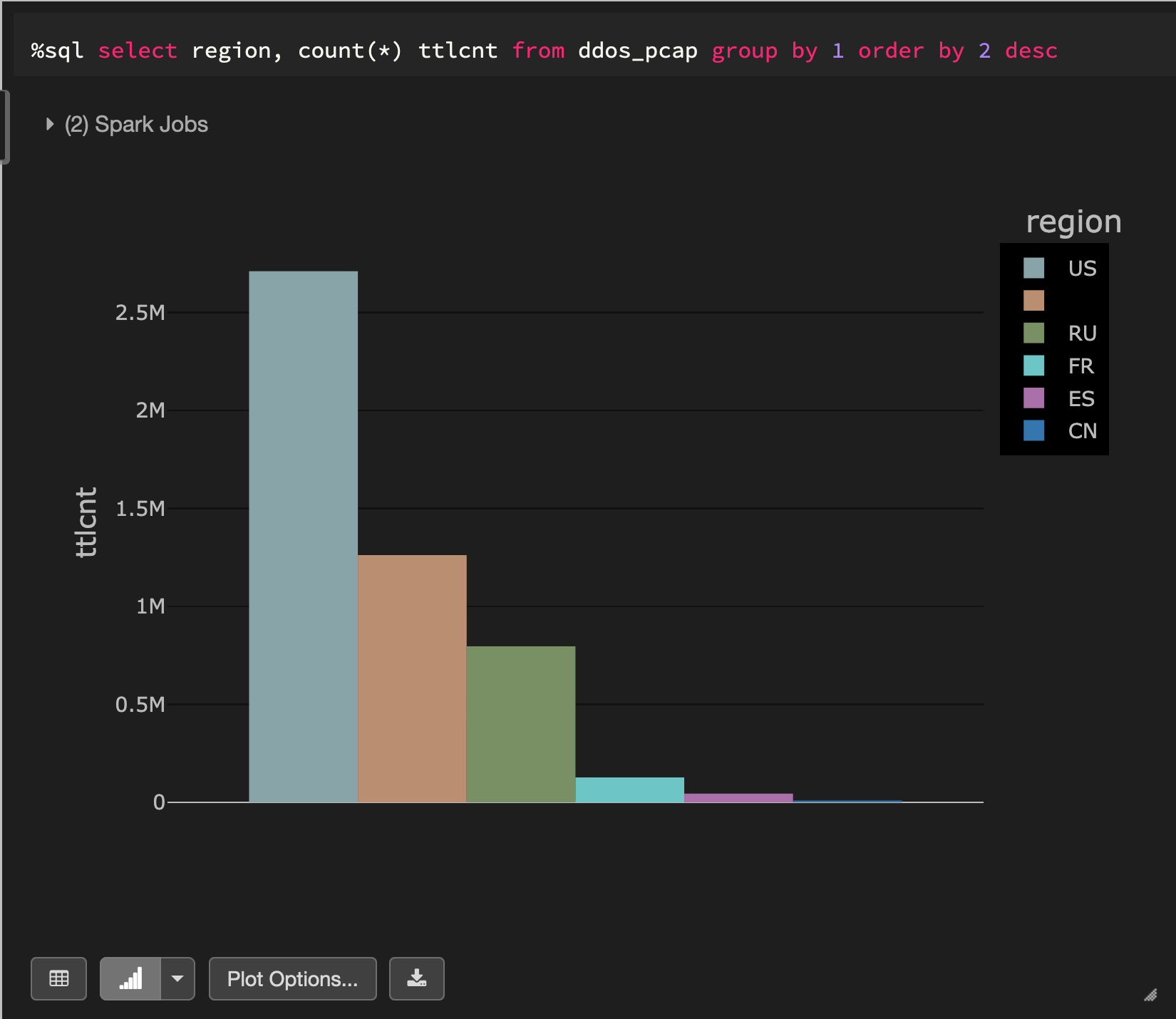
The above knowledge illustrates packet captures throughout a simulated distributed denial-of-service (DDoS) assault. So as to make this a regional-based simulation, we are going to generate a rustic code for every report. Right here’s how the info breaks down by nation code:
Now that we’ve established what the info set seems like, let’s dive into how Immuta helps allow Zero Belief.
Immuta is an automatic knowledge entry management resolution that was born out of the U.S. Intelligence group. The platform permits you to construct dynamic, scalable, and simplified insurance policies to make sure knowledge entry controls are enforced appropriately and constantly throughout your whole knowledge stack.
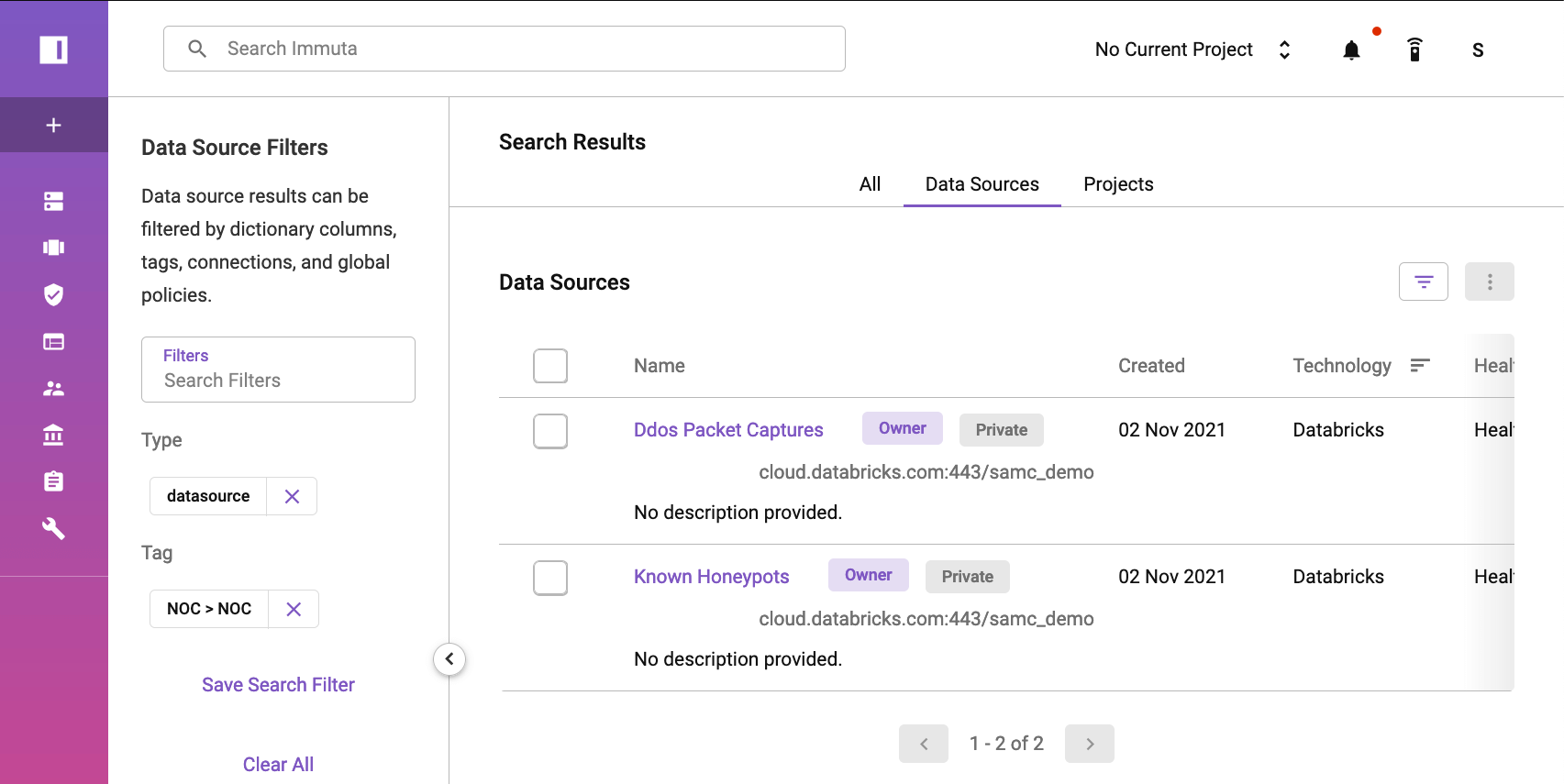
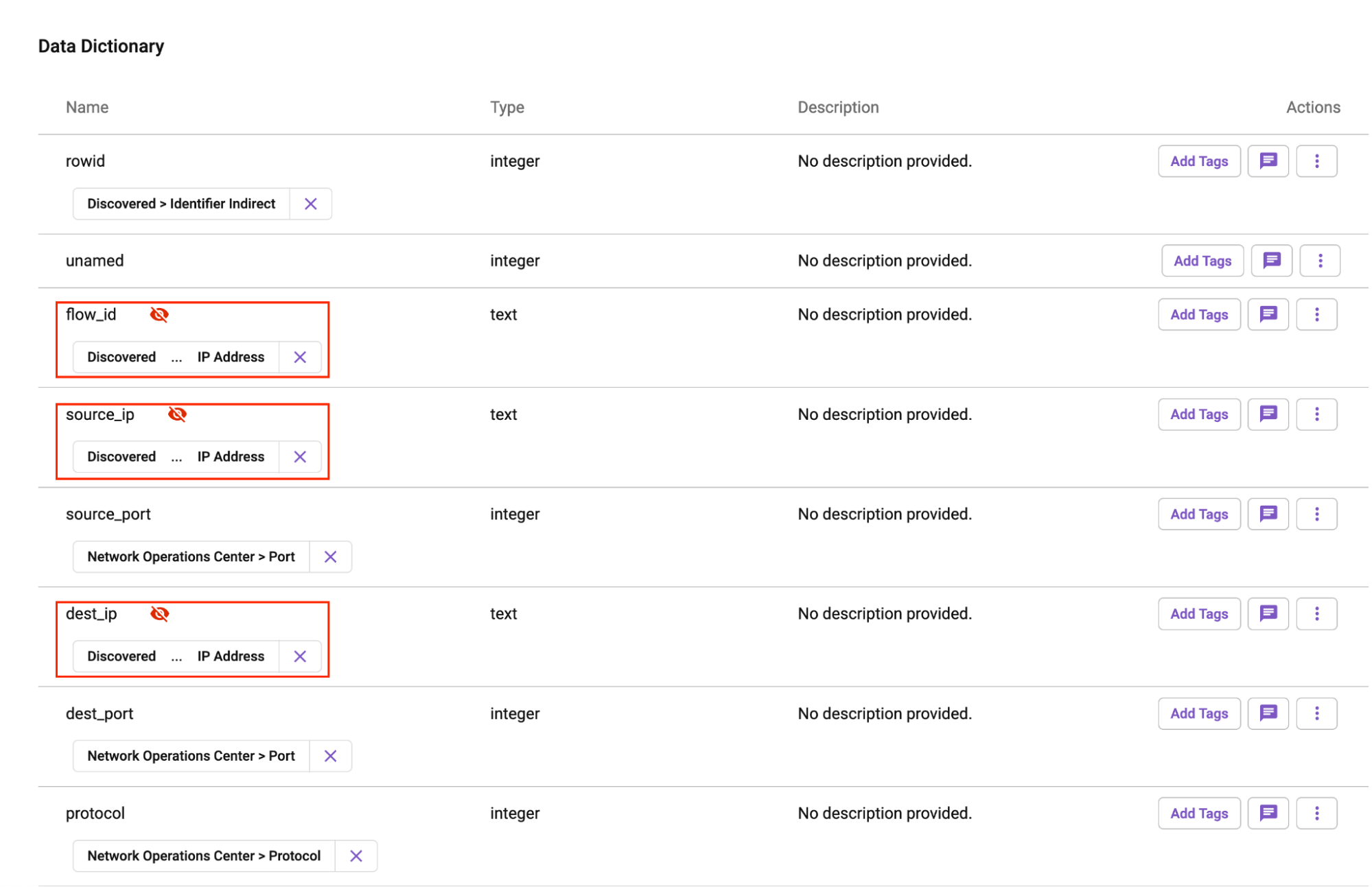
Step one to guard this PCAP knowledge set is to register the info supply in Immuta. This registration merely requires inputting connection particulars for our Databricks cluster. As soon as full, we are going to see the info units in Immuta:
As soon as this desk has been registered, Immuta will routinely run delicate knowledge discovery (SDD). This step is vital, as we might want to stop sure customers from seeing delicate data. On the PCAP desk, SDD recognized a number of several types of sensitivity within the knowledge set, together with the IP addresses, personally identifiable data (PII), and site knowledge within the area column.
Now that we’ve labeled the info utilizing SDD, let’s construct knowledge insurance policies to make sure the delicate data from the packet knowledge is masked. Immuta gives many dynamic knowledge masking strategies, however on this case we are going to use an irreversible hash. In the true world, it may not be necessary to see the precise values for an IP handle, however the hashed values nonetheless should be constant and distinctive. That is necessary for 2 causes:
- Analysts want to make sure they will decide if a particular IP handle is inflicting a spike in community visitors.
- Any knowledge set containing IP addresses should be constant. For instance, think about we’ve got a desk with honeypot server data that may have to be joined to on a hashed key. Immuta permits customers to carry out masked joins whereas making certain delicate data is protected utilizing “tasks.” Consistency throughout knowledge units ensures no delicate knowledge slips by the cracks in a collaborative undertaking scenario.
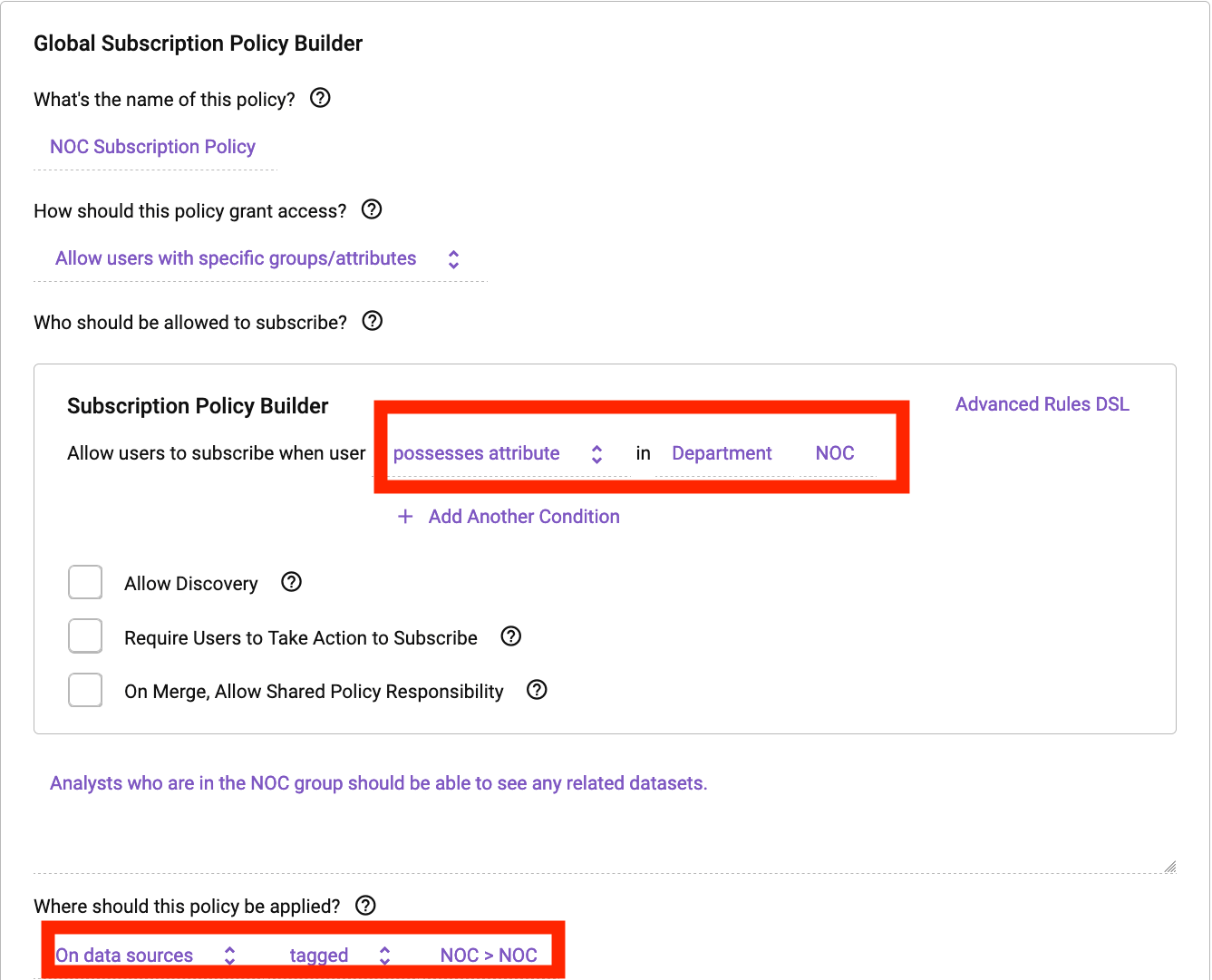
The instance beneath reveals how straightforward it’s to make sure a person has least privilege entry, which means no person has default entry to any knowledge set in a Databricks cluster protected by Immuta. Knowledge homeowners can specify why somebody ought to get entry to the info, whether or not or not it’s for a authorized goal they should attest to or primarily based on group membership or person profile attribute. In our instance, we are going to permit any person with a Division of “NOC” on their person profile to see this desk in Databricks. With Immuta’s plain English coverage constructing capabilities, a coverage is as straightforward to know as studying a sentence. Think about the next subscription coverage:
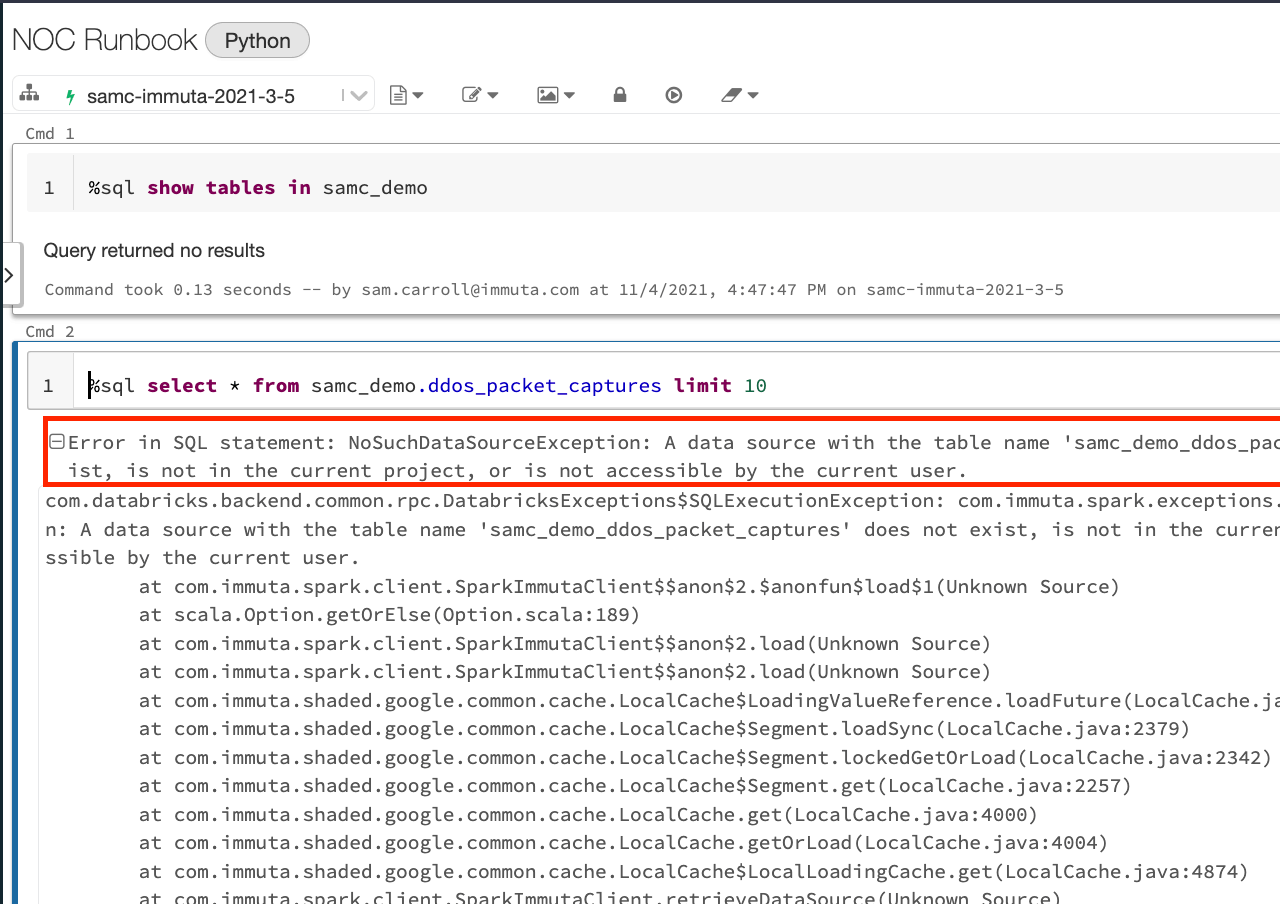
This coverage will routinely dictate who can see any desk that has been labeled as “NOC” transparently in Databricks. Beneath is the Databricks pocket book for somebody who doesn’t have the subscription coverage utilized:
The person can’t see any tables in Databricks, and in the event that they attempt to question the desk immediately, they get a permission error. This least-privilege idea is core to Immuta and one of many causes it could assist allow Zero Belief in Databricks.
Subsequent, let’s allow the subscription coverage and see what occurs:
As you possibly can see, the person now will get entry to the PCAP desk and an extra honeypot desk as a result of it was labeled as a NOC knowledge set. That is useful when onboarding new customers, teams, or organizations, because it proactively and dynamically lets customers see knowledge units which can be related to their jobs, whereas making certain they will entry solely these knowledge units they really must see.
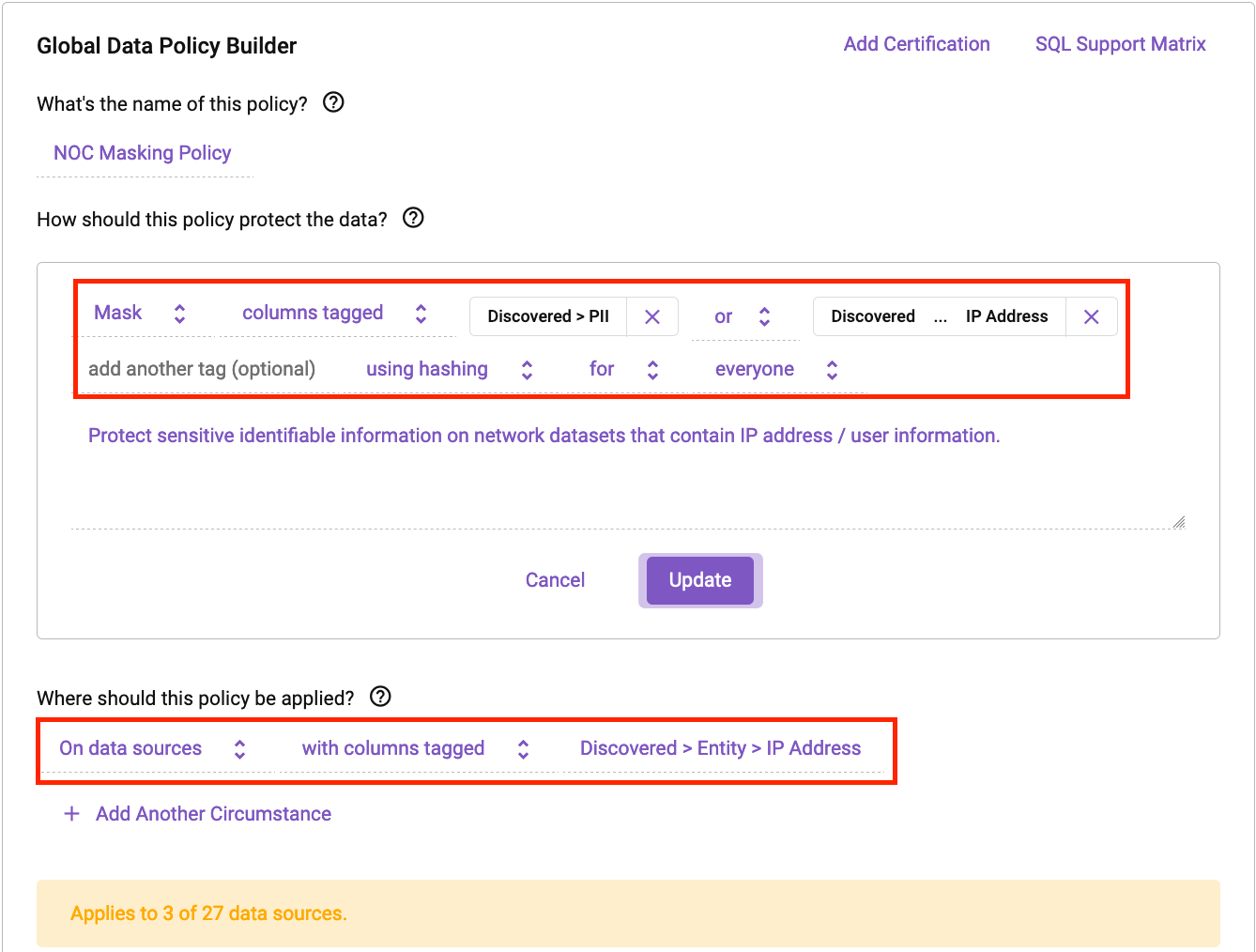
Subsequent, let’s construct a coverage to additional shield the info and guarantee customers don’t by accident uncover any delicate knowledge on this Databricks setting. Beneath is an easy knowledge masking coverage in Immuta:
Within the above instance, we are able to see how straightforward it’s to make guidelines that may shield your NOC knowledge units. Any knowledge set containing an IP handle will now routinely have the IP handle or PII masked for anybody within the group utilizing Databricks. This ensures that your knowledge is protected in a constant method.
Now that we’ve outlined a single coverage that may be utilized to all of our Databricks knowledge units, let’s check out what occurred to our honeypot desk talked about earlier:
Discover how all of the IP handle data and PII are dynamically masked. That one coverage is now utilized constantly throughout two totally different tables as a result of their context is similar.
Subsequent, let’s see how we are able to guarantee least privilege entry much more granularly by solely permitting customers to see the areas they’re licensed to see. Presently, customers can see knowledge from all international locations of their knowledge set:
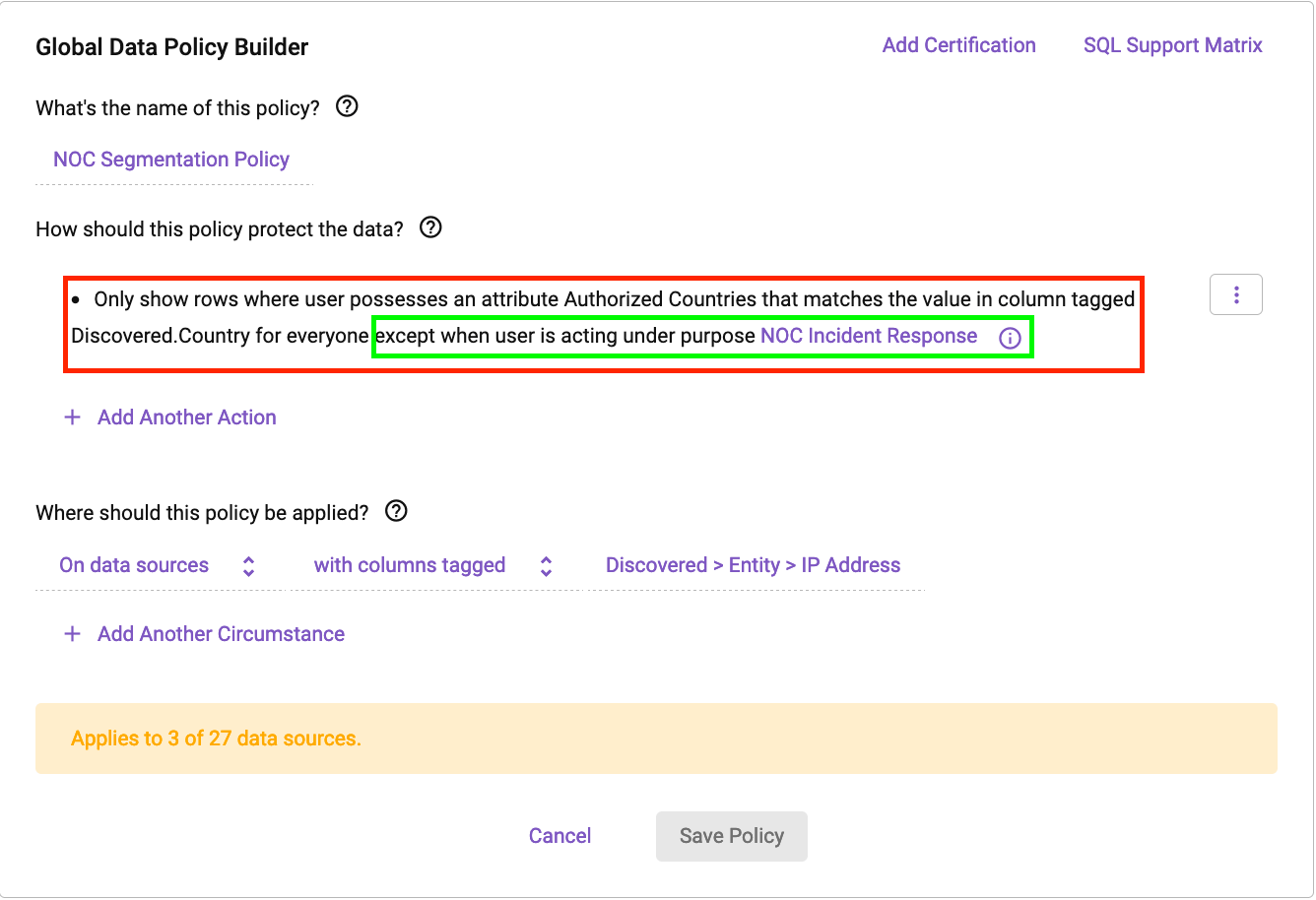
We’ll construct a segmentation coverage in Immuta that makes use of an attribute derived from an id supervisor (on this case, Okta):
This coverage states that we are going to use “Approved International locations” from a person’s profile to dynamically construct a filter that matches any column tagged Found.Nation on any knowledge set containing an IP handle subject.
Subsequent, let’s dig into the exclusion rule (in inexperienced). The exclusion rule states that customers received’t see filtered knowledge when they’re working below a “Goal” context. This goal context states that if an analyst is engaged on an incident response, they’re licensed to see unfiltered location knowledge. Functions have many makes use of in Immuta, together with permitting customers to raise their knowledge entry privilege when needed for a particular, permitted motive. Modifications like this are audited, and customers can replace contexts immediately in a Databricks pocket book.
Now that this knowledge coverage has been constructed, let’s dive into what it’s going to do to our PCAP knowledge set:
Now this person is seeing solely the international locations they’re licensed to entry, thus limiting their entry to the least quantity of information they need to see. Let’s examine one other person to see what their knowledge seems like:
This person is seeing constant masking, however for the set of nations that they’re licensed to entry.
Lastly, let’s check out the exclusion rule we set earlier. Think about a cyber assault has simply occured and our analyst must view community visitors for the complete firm, not simply their areas of authorization. To do that, the person goes to modify context into the “Incident Response” goal:
The person in Databricks up to date their “undertaking” context to “Incident Response.” This context will get logged in Immuta and when the person runs their subsequent question, they may see all areas inside the PCAP knowledge set as a result of they’re working below this Goal. Now you, because the NOC analyst can detect DDoS assaults originating outdoors of your default entry stage.
We’ve walked step-by-step how rapidly Immuta allows least privilege entry on Databricks however to see this course of in motion, you possibly can watch a demo right here. Immuta supplies compliance officers assurance that customers will solely be granted entry to the data for which they need to have entry to, whereas sustaining strong audit logs of who’s accessing what knowledge supply and for what motive. Using each Databricks and Immuta permits NOCs to allow a Zero Belief structure on the info lake. To get began with Databricks and Immuta request a free trial beneath:
[ad_2]
![Example of masked data set]](https://databricks.com/wp-content/uploads/2022/03/db-91-blog-img-13.jpg)